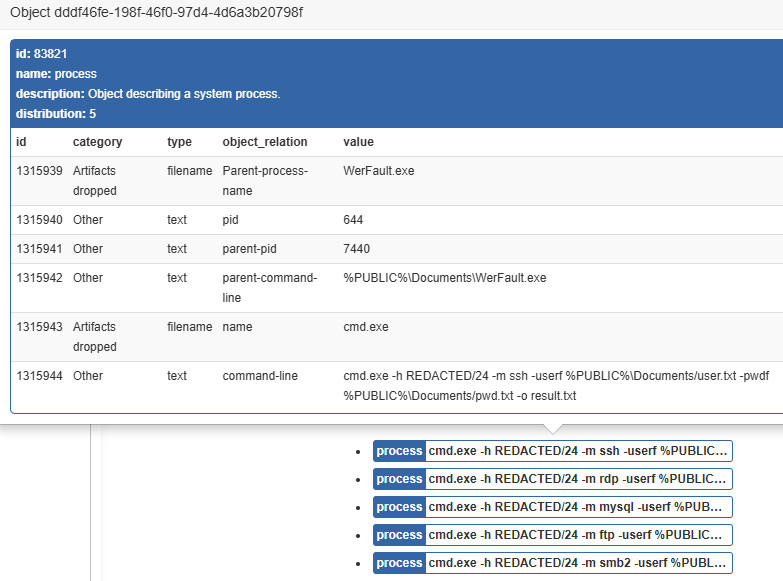
"The threat actor executed ipconfig /all to gather network configuration details. Shortly after, we observed network scanning behavior and brute-force attacks across the 10.xx.xx.0/24 subnet.
Targeted services included SSH, RDP, MySQL, MSSQL, FTP, and SMB."
1/3
Targeted services included SSH, RDP, MySQL, MSSQL, FTP, and SMB."
1/3
Comments
The commands and argument order point to the use of the scanning tool fscan."
2/3
"From Resume to Recon: Threat Actor Uses WerFault for Pupy RAT Deployment"
📄Read more about our services: https://thedfirreport.com/services/
📞 Contact us: https://thedfirreport.com/contact/
3/3