2/ How the attack works:
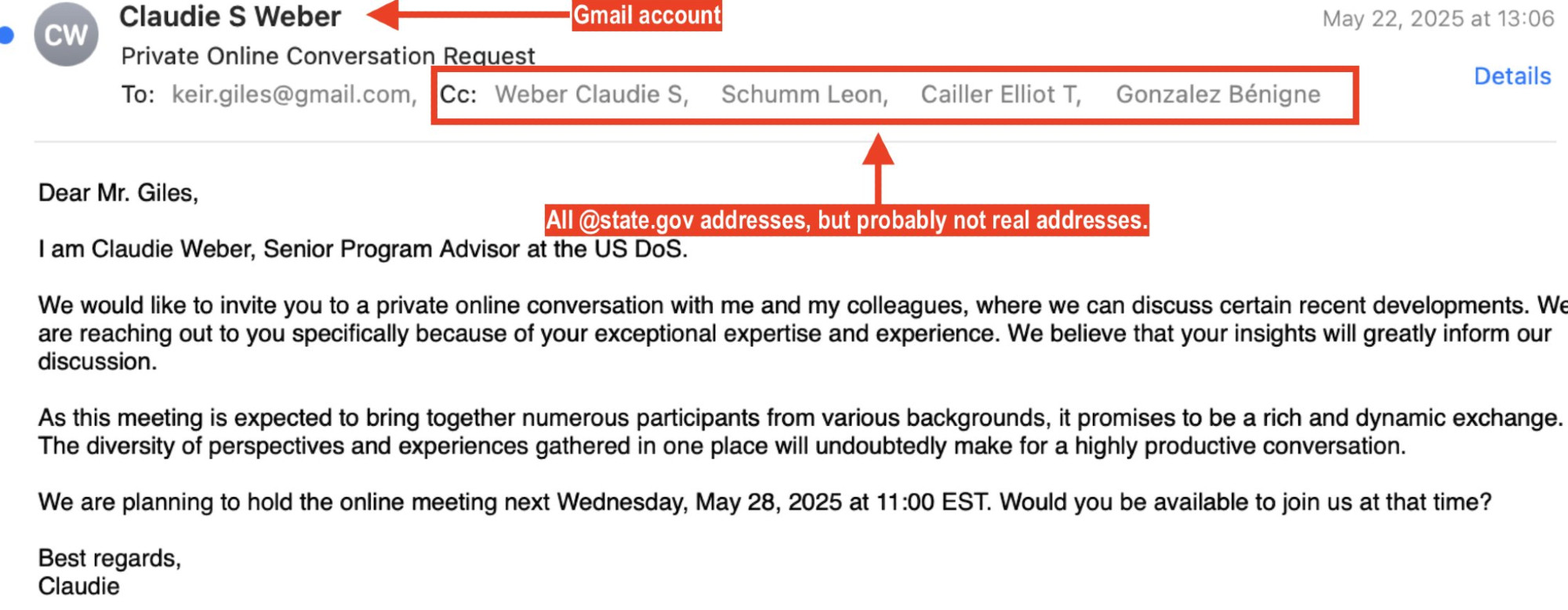
First. @keirgiles.bsky.social gets a message purporting to be from the State Dept asking for a consultation.
Pretty common thing for him.
And these attackers did everything to make this outreach look credible...
Like CCing a bunch of @state.gov email addresses...
First. @keirgiles.bsky.social gets a message purporting to be from the State Dept asking for a consultation.
Pretty common thing for him.
And these attackers did everything to make this outreach look credible...
Like CCing a bunch of @state.gov email addresses...
Comments
Well, the #Russian attackers must've figured out that the State Dept mailserver just accepts all email to ANY @state.gov address without a bounce.
So they just added some fake State Dept staff names and addresses.
Smart!
In the next days they patiently walk him through what they want him to do, even sending a very official looking (but fake) State Dept. document
@keirgiles.bsky.social into creating & sending the attacker an App-Specific Password (ASP).
They do this by reframing ASPs as something that will let him access a secure resource (spoiler: not how this works)..
So, what IS an ASP for real tho?
Some older email clients don't. So providers like Google let users create a special password just for those apps.
An ASP is a string of characters that give access to *everything*
See where this is going?
Very much not your run-of-the-mill phishing.
Ultimately, @keirgiles.bsky.social realized something was wrong and got in touch with us @citizenlab.ca...but not before the attackers got some of his ASPs...
Threat Intelligence Group w/analysis & attribution!
Great!
Our bad actors are: 🇷🇺 #UNC6293, a #Russian state-sponsored threat actor.
Google adds bonus additional low confidence association to #APT29 (that would be the #SVR).
Nice people.