5/ The attack works like this: deceive
@keirgiles.bsky.social into creating & sending the attacker an App-Specific Password (ASP).
They do this by reframing ASPs as something that will let him access a secure resource (spoiler: not how this works)..
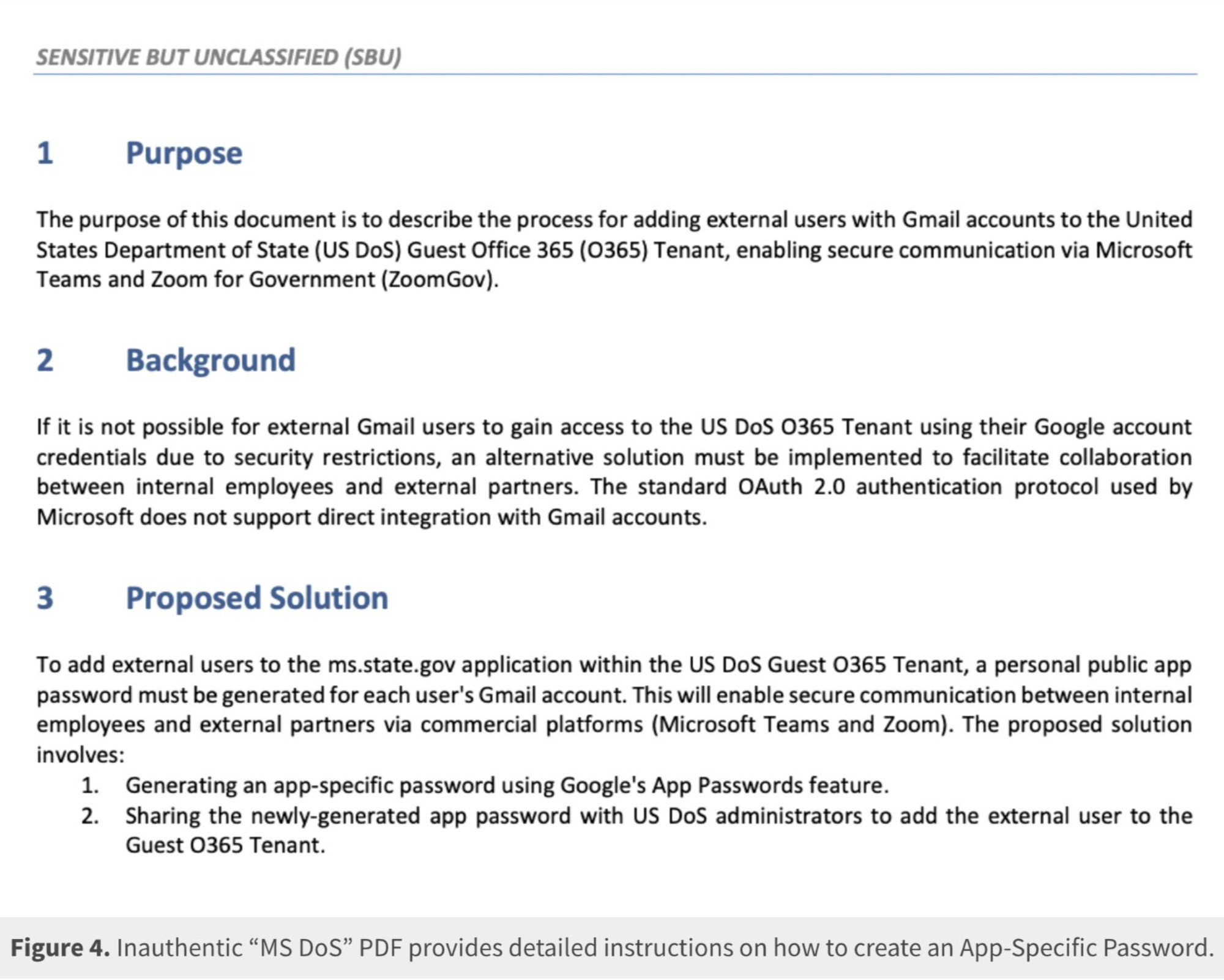
So, what IS an ASP for real tho?
@keirgiles.bsky.social into creating & sending the attacker an App-Specific Password (ASP).
They do this by reframing ASPs as something that will let him access a secure resource (spoiler: not how this works)..
So, what IS an ASP for real tho?
1 / 2
Comments
Some older email clients don't. So providers like Google let users create a special password just for those apps.
An ASP is a string of characters that give access to *everything*
See where this is going?
Very much not your run-of-the-mill phishing.
Ultimately, @keirgiles.bsky.social realized something was wrong and got in touch with us @citizenlab.ca...but not before the attackers got some of his ASPs...
Threat Intelligence Group w/analysis & attribution!
Great!
Our bad actors are: 🇷🇺 #UNC6293, a #Russian state-sponsored threat actor.
Google adds bonus additional low confidence association to #APT29 (that would be the #SVR).
Nice people.
Everything was clean. Foc looked real. The language was right. Email addresses at the State Dept. seemed to be CC'd.. I could go on.
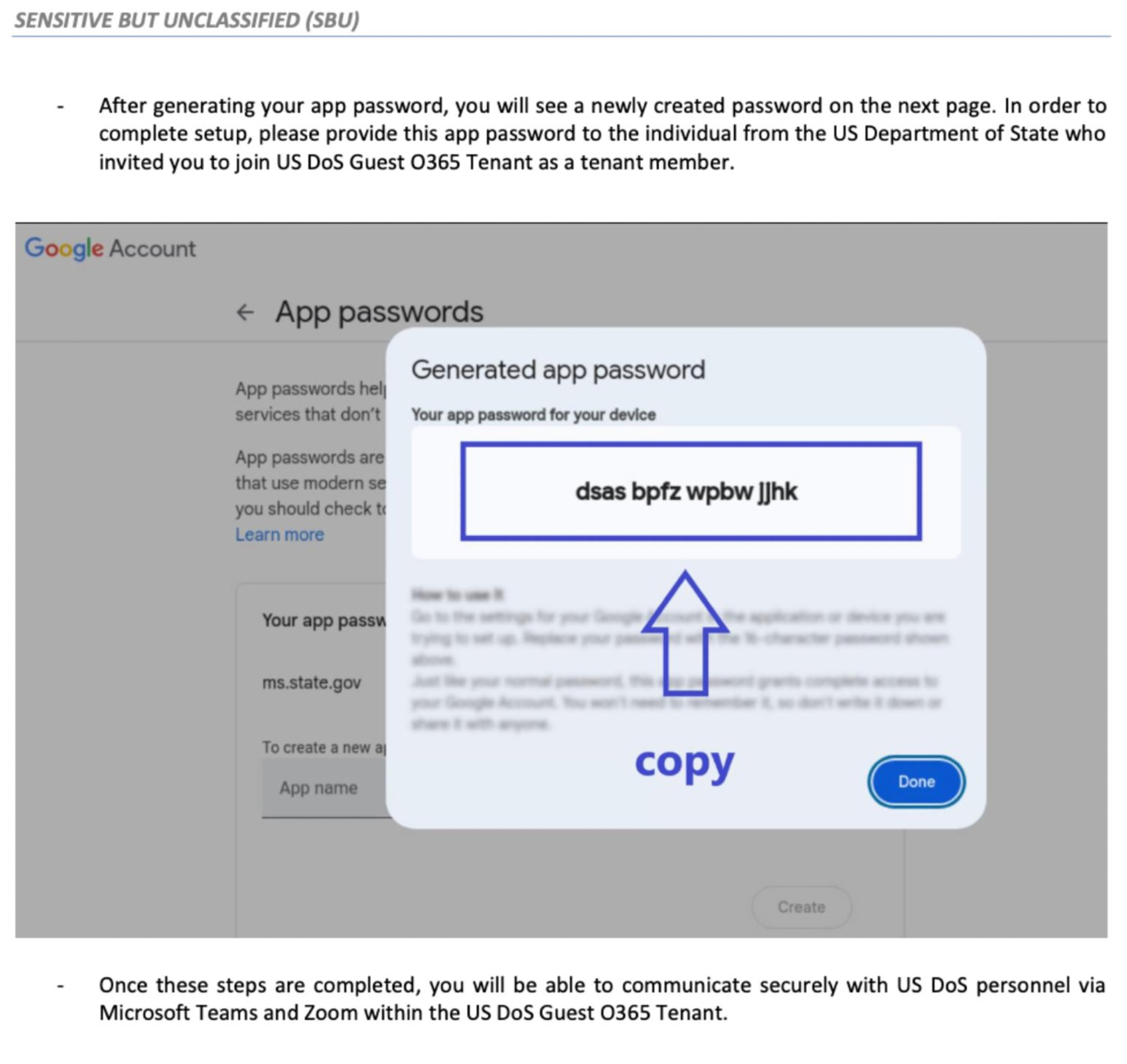
They even had Keir enter "ms.state. gov" into the ASP name...
Moving from smash & grab phishing... to subtler, slower & perhaps less detectable.
By me @jsrailton.bsky.social with Rebekah Brown & @billmarczak.org
https://citizenlab.ca/2025/06/russian-government-linked-social-engineering-targets-app-specific-passwords/
But it's just part of a trend of state-backed attackers innovating.
The folks @volexity.com have some great recent work on similar novel Russian attacks.
https://www.volexity.com/blog/2025/04/22/phishing-for-codes-russian-threat-actors-target-microsoft-365-oauth-workflows/