==Training Lesson==
INVESTIGATION NARRATIVE: SSH Kill la Killed 🧵
My job is to solve the Weird Problems as the Final escalation tier. I do this with generalist knowledge and practical experience.
New InfoSec/IT entrants often ask what this looks like in practice. Follow below.
INVESTIGATION NARRATIVE: SSH Kill la Killed 🧵
My job is to solve the Weird Problems as the Final escalation tier. I do this with generalist knowledge and practical experience.
New InfoSec/IT entrants often ask what this looks like in practice. Follow below.
Comments
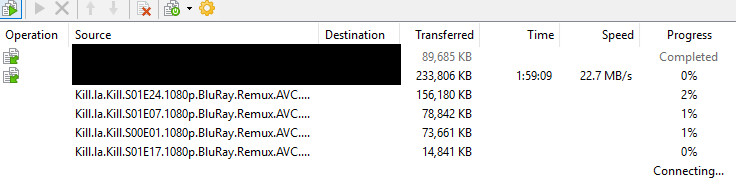
I have a seedbox in Europe to coalesse torrent downloads from other servers at 10gbe uplink to many other similar colocated servers hosting the content. I then collect finished over SSH file copy at my leisure.
I go into WinSCP and turn this on, 6 sounds good.
It starts opening them... and then the last one is stuck at connecting. And the others die?
Servers have anti-abuse mechanisms you can trip. This one doesn't.
"But SSH is encrypted."
Troubleshooting is often connecting metadata.
I have never troubleshooted WinSCP or SSH before, Wireshark for years but don't use often, and my networking is really fundamentals and "weird stuff I've run into."
Importantly, I know what Normal looks like.
Lab when we were trying out Wireshark for a computer lab at college didn’t get far they had us shut it down
(After it makes the rounds that it’s the network’s fault and maybe the network team should just make these pages work somehow)
Mute this thread? This is extremely my area of interest.
The autistic desire to…
The various jobs I’ve done? A breadth of experience with a whole bunch of different systems that I’ve broken down to understand how they fit together.
Now I find myself identifying edge cases.
If you give me a broken system, I will find an edge case, and I will file a Jira for the devs.